Dell Security Survey – VMUG Member Insights
With the continued threat of cyberattacks and ransomware events, cyber-security is top of mind for most IT personnel. There has been an increase in cyber threats, with more sophisticated attacks, becoming an increasing concern for IT departments. Seventy-four percent of IT decision makers see a greater risk with the growing trend for remote work. Their top concerns are malware, ransomware and protecting cloud-native apps. (Source: Dell Technologies Global Data Protection Index). Add to this, the average cost per company of data loss and downtime is approaching $1.5M, compounding the concerns for key stakeholders and decision makers. In some cases, the damage to the brand can’t be measured.
September 11, 2001, the World Trade Center attack resulted in significant impacts to IT infrastructure. This taught organizations to focus on disaster recovery. We duplicated our infrastructure and replicated it to off-site facilities, miles (even regions) away from onsite production.
Now, we still plan for physical disasters, but we must plan on cyber disasters, too. Security Operations (SecOps) are everyone’s responsibility. The data companies acquire is more important than ever, and protecting that data is crucial.
With this being a growing issue, and clearly a concern for so many IT professionals, what are we doing about it? Recently Dell Technologies sponsored a survey of your peers and VMUG members.
First, it is important to use a framework. Thirty-two percent (32%) of respondents said their company uses the NIST framework and 20% reported using the MITRE ATT&CK® framework. This is a good starting point of vetted processes to understand how your company matches up.
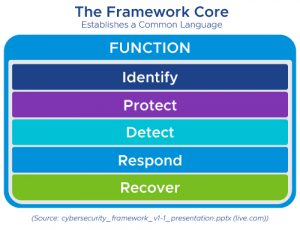
The National Institute of Standards and Technology (NIST) develops cyber-security standards, guidelines, best practices, and resources to meet the needs of U.S. industry, federal agencies, and the broader public. The NIST Framework Core is: Identify, Protect, Detect, Respond, Recover, as shown in the graphic below.
The MITRE ATT&CK® framework is largely a knowledge base of adversarial techniques. It does not focus on the tools hackers use, but how those tools and hackers interact with the system. The framework has a matrix that visualizes the relationship between tactics and techniques. You can learn more at their ATT&CK 101 Blog.
Having a Security Information Event Management (SIEM) solution is common. Over half (55%) of respondents are planning to use a purchased or an outsourced SIEM solution. These solutions allow for automating the analysis of multiple sources of data for 24×7 monitoring. A smaller number (13%) of respondents use an in-house-developed SIEM solution. Unless this is your core business or you have a specific use case, this is not recommended.
Surveyed peers and VMUG members reported that ‘disaster recovery and remediation practices’ (49%) are the top 2022 security initiatives, followed by the ‘ability to recover after a destructive cyber-attack’ (40%). This data supports the widely accepted view that a cyber-incident is a matter of when, not if. Our ability to recover from such an incident must be anticipated and planned. I agree with Dell’s point of view:
Cyber-resilience is the ability to maintain business continuity despite cyber-attacks. It encompasses the real-world view that, despite your best efforts, breaches may occur. And when that happens, your organization must be able to quickly recover lost or compromised data, restore system functionality and resume business activities.
(Source: https://www.vmug.com/protect-and-preserve-your-data-from-endpoint-to-infrastructure)
Members are following the NIST framework core plan to use automated detection and response, cloud-based security services, and managed security services to prepare (44%, 43%, 36% respectively). These top three can all be delivered as a service (aaS), allowing you to focus on your core business.
The top threat of concern is Ransomware/Malware (50%). One method for ransomware recovery is deploying an air-gap solution. While isolating your data from the internet adds protection, you still need to use advanced security technology. Dell’s Endpoint Security offers Full Air Gap mode allowing advanced threat protection, without requiring an internet connection.
The second concern is Phishing attacks (43%). A threat detection and response solution (TDR) is designed to help detect, investigate, and respond to phishing attacks. Managed Detection and Response (MDR) is a Managed Services Security Provider (MSSP) solution where the vendor does the monitoring for you. An attractive solution for many who cannot afford 24×7 monitoring. Dell and VMware have teamed up for an MDR solution that includes SecureWorks and VMware Carbon Black NGAV (Next-Generation Antivirus) solutions.
Just as internally managing Exchange has moved to aaS, companies are not handling security by themselves. Many (79%) say they will use a Managed Services Security Provider (MSSP) and 81% of those using a SIEM will use a third party. The top three reasons for using an MSSP (31% for each) are 24×7 endpoint security monitoring, threat detection and response, and vulnerability and patch management.
We all agree security is top of mind. And securing endpoints is at the top of security concerns. This blog just scratches the surface to protect endpoints. To find out more, consult these documents and solutions from Dell Technologies.
- Endpoint Security Solutions – PC Security | Dell Technologies US
- https://www.delltechnologies.com/asset/en-us/solutions/industry-solutions/briefs-summaries/h18894-dell-vmware-infographic-security.pdf
- https://www.delltechnologies.com/asset/en-us/solutions/industry-solutions/briefs-summaries/h18999-dell-vmware-pov-security.pdf
- Global Data Protection Index Report | Dell Technologies US
- The Pathway to a Zero-Trust Security Model (delltechnologies.com)
It’s important to note, security is not just a technical problem. It requires both a technical and non-technical solution that includes employee training, awareness, and testing. SecOps is everyone’s responsibility, even those not in IT.
Brad Tompkins
VMUG Executive Director
@BradTompkins_ (Twitter)
Security Survey Methodology
Campaign Dates: 10/21/2021 – 11/19/2021
Engagement Audience: 594 VMUG members

